Start
Case prep 1
Case prep 2
Data and power cables
Serial ATA stuff
General motherboard/CPU info
Testing & installing the motherboard assembly
Installing the hard drive
Final connections
Security during Windows Setup
Best practices for ongoing security
Resources (drivers, diagnostics, links, online antivirus scans, antispyware resources)
A brief visual glossary
|
back to the Windows Setup Security page
 Netgear RP614, a basic router for about US$40. Your modem plugs into the WAN port on the rear, and your computer(s) plug into the four LAN ports.
Netgear RP614, a basic router for about US$40. Your modem plugs into the WAN port on the rear, and your computer(s) plug into the four LAN ports.
Why should I get a router? This page assumes you have a broadband Internet connection (cable, DSL, satellite), rather than old-fashioned dial-up. If you do have dial-up, use software firewalls on your computers, such as the Windows Firewall.
Your router will prevent unauthorized computers and hackers from using your Internet connection to attempt to make direct contact with your own computers. The router is like the security people at the airport who make sure you have a boarding pass, before they let you proceed to the security scanners. If you don't have a boarding pass, you won't get any farther. Likewise, if a computer on the Internet tries to contact your own computer to hack it or infect it, your router will check to see if your computer requested the contact. If not, the router will ignore the outside computer.
Important configuration advice In recent times, the bad guys have developed ways to attack routers and broadband modems using creative techniques, such as infected banner advertisements on Web pages. It's fairly easy to stop them. You should use a Web browser to access the configuration menu for your broadband modem, and also your router, and do three steps as needed:
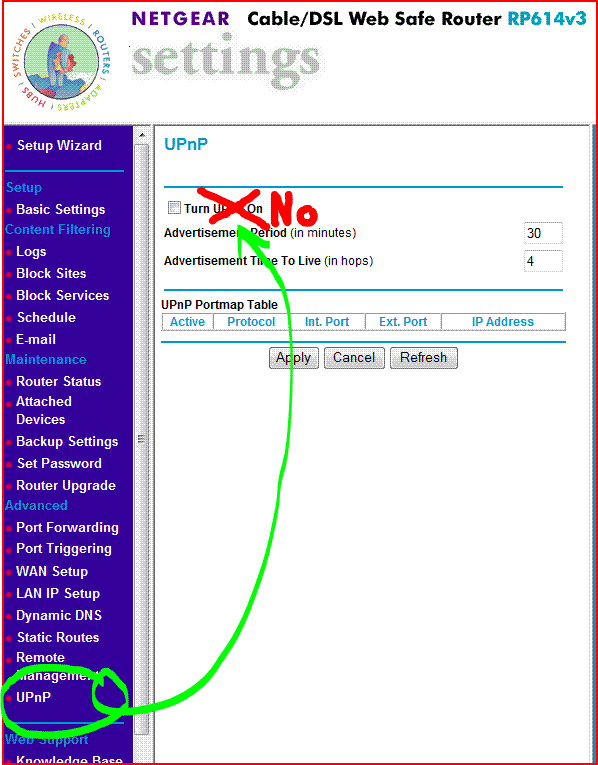
Disable the feature called Universal Plug 'n Play (UPnP) on both the router and the modem. Some modems don't have UPnP.
Change the passwords for the modem and the router to strong passwords (8 characters or longer, and containing at least one numeral (0-9) and one symbol).
Disable or secure any wireless capabilities on both the modem and the router. If you do use wireless yourself, only enable wireless on your router, not your modem. Choose the highest level of wireless encryption that your router and computers can use (WPA or WPA2, if possible), and enable MAC address filtering so only your own individual computers are permitted to connect (each individual computer normally has a unique MAC address, like a fingerprint). See the router's manual for help with this.
OK, I'll try that. How do I log onto my modem and my router with a Web browser? In your Web browser's address bar, you type the addresses for your modem and your router as if they were web sites.
Typically, your modem will be http://192.168.0.1 or http://192.168.1.1. If you are prompted for a username and password, look in the owner's manual of the modem or router for the default username and password.
If you have a router already, one way to determine its address is to log onto your computer as an Administrator, open a Command Prompt from the Start > All Programs > Accessories menu, and run the command ipconfig /all, then look at the default gateway line, and use that address. Again, the default username and password will be in the owner's manual, and the fact that they are public knowledge is the reason that you want to change the password to something else.
Why is a router recommended when my PC already has a software firewall? Isn't that redundant?
Resistance to attack Unlike the Windows Firewall or other software firewalls, the router's inbound firewall capabilities normally cannot be disabled or modified by a virus or worm.
Protect multiple computers and share your connection easily Budget routers typically have a four-port network switch built into them, so you can plug in up to four computers without needing to buy a separate switch or hub. All of the computers will be protected from outside attackers on the Internet. If you need wireless capabilities, you can buy a router with wireless and the router's firewall will also shield your wireless computers from outsiders. NOTE: the router's firewall does not protect your own computers from each other, which is why you should still have software firewalls on each of your computers, as a precaution.
Keep attackers as far away as possible The router keeps outside computers on the Internet from directly interrogating your computer(s) to try to feed them worms, hack them, send them infuriating dialogue-box Spam messages, or discover anything about them (what Windows version they have, whether they have services running, etc). Most routers will not even respond to a ping, making it appear there's no network at your address.
Damage containment (for advanced users) If your computer does get infected, the malware may attempt to "phone home" for more malware to install, and instructions on what to do next. Naturally it will begin trying to find more computers to infect, too. By default, your router allows this, because the traffic is initiated from "inside." You can lock down your router to only allow traffic on ports (channels) that you actually need open, and this creates an insurmountable obstacle to many worms that are pre-programmed to use specific or random high-numbered ports that you happen to have locked. There's more information on this lockdown subject below.
|
|
Advanced users: locking unnecessary TCP/IP ports completely There are 65535 ports, which could be thought of like channels on a television perhaps. Worms, backdoors and Trojans are often designed to use random or specific high-numbered ports to "phone home" and report for duty. Once they can get a connection to their boss for further instructions, they may download more malware, perform DDoS attacks, send Spam, host a fraudulent "phishing" website on your computer, or other Bad Stuff™. If you can stop the "phone home" stage by closing ports that you have no need for, that's better than nothing.
With that in mind, let's look at that Netgear RP614 since I have one to use as an example. You can do similar stuff with the popular models from Linksys (BEFSR41) and D-Link (DI-604) too. Here are the ports I would have uses for:
- 20 and 21 for FTP
- 25 for SMTP email
- 53 for DNS
- 80 for standard HTTP web browsing
- 110 for POP3 email
- 123 for NTP (network time protocol so WinXP can sync to official time servers) obviously optional here
- 443 for secured HTTPS web browsing
So I can create rules on the Netgear that block TCP and UDP traffic on all the ranges of ports I don't need, as shown in the picture above. If I want to know what port I need to permit to allow a certain program (a game, an instant-messenger program, etc), I'd just do a Google search for name of program firewall port.
|
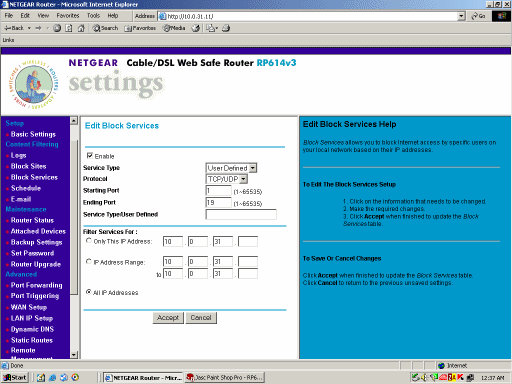
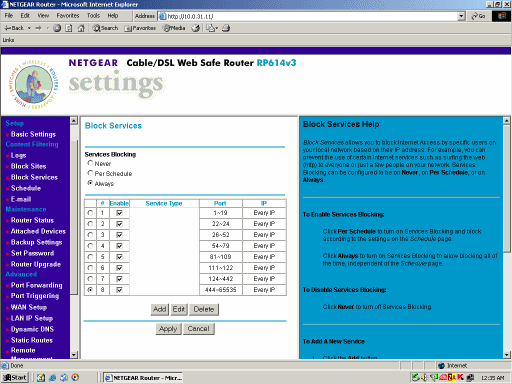
Here's the first rule I made, which blocks TCP and UDP traffic both ways on ports 1 through 19. My computer has no legitimate reason to be communicating with the outside world on these ports.
|
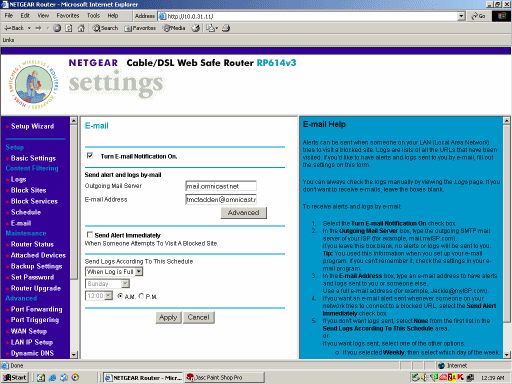
I can also set up the router to email its logs to me. If I see my computer trying to "get out" on weird ports non-stop, that could indicate a problem.
|
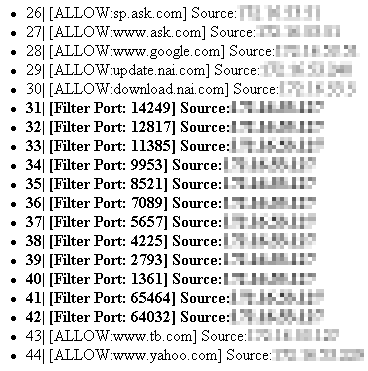
Some log output from an RP614 showing the filter in action. It will also show inbound packets that the Stateful Packet Inspection (SPI) found to be suspicious.
Obviously this is not completely worm-tight, since worms could still make outbound connections on the ports I left open out of necessity, but it will narrow the options a great deal.
|
back to the Windows Setup Security page
|
 ©
©
 ©
©